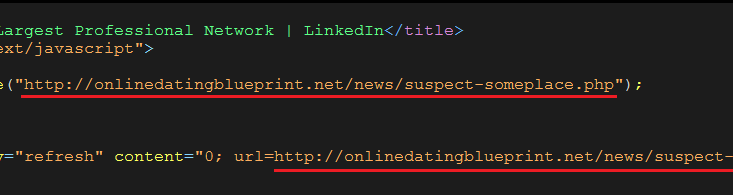
Security Alert 2013-09-05:The secrets of Android malware, a true story
Over the last month, many smartphone users in Taiwan received an SMS message concerning personal privacy. The message entitled "You were shot by paparazzi!" and contains a URL, such as hxxp://199.101.117.21/index.php, to download a malicious APK. AegisLab has analyzed the characteristic of the APK and released the malware signature to our customer at the first time. The […]



 Follow
Follow