Recently, Bluebox Security announced there is a vulnerability in Android that allows a crack to modify APK code and bypass the APK certificate mechanism. The vulnerability is named Master Keys Vulnerability and will be released by Bluebox Security at Black Hat USA 2013.
(http://bluebox.com/corporate-blog/bluebox-uncovers-android-master-key/)
After AegisLab analysis, some of Sony and Samsung using Android 4.2 had been patched already. And here comes the technical details:
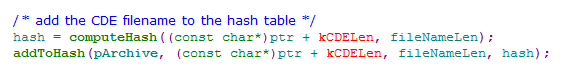
The key point is the duplicated entries of classes.dex in ZIP(APK) file. There are two classes.dex files: the modified one(07-09-2013) and the original one(03-13-2013). The modified classes.dex MUST be put before the original one.
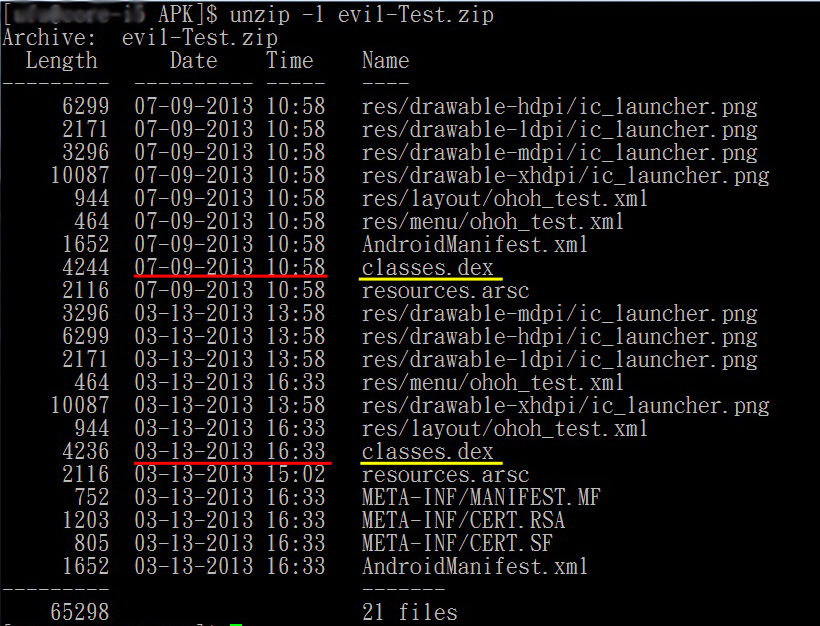
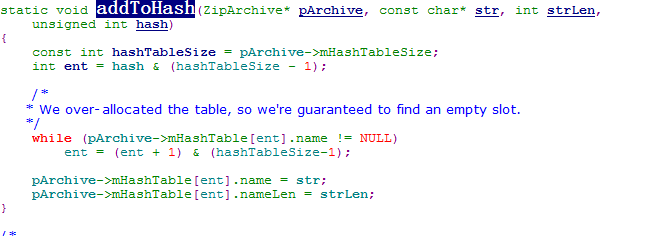
When install a APK file, Android will check the APK's certificate. The main function is the mEntries struct of ZipFile. When reading ZIP file, it will find Zip Central Directory Entry. Make Name as index, put it to LinkedHashMap by the entry order:
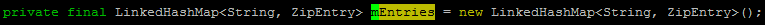
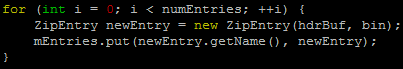
LinkedHashMap will return old value and maps to the new value if index collision.
Therefor, it certificate the original classes.dex
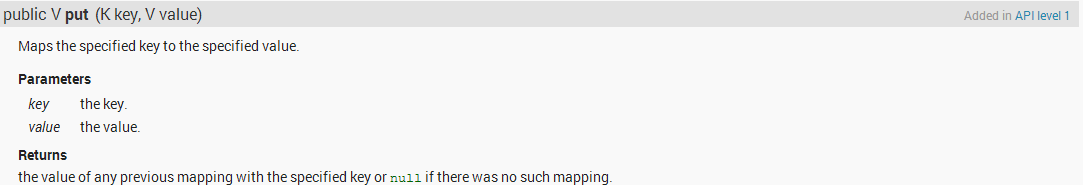
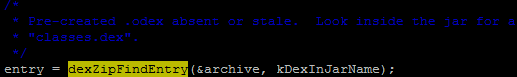
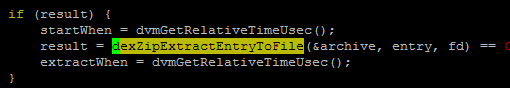
When run a APP, here are the key steps:
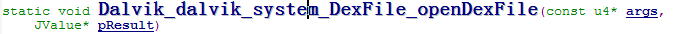
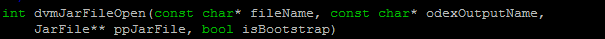
Open ZIP file
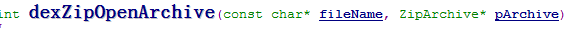
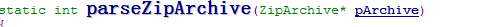
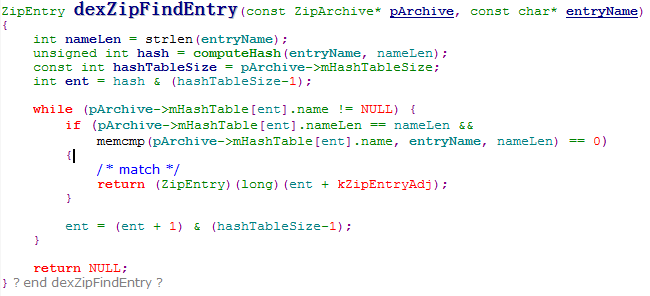
Find DEX in ZIP file, USING THE ZIP ENTRY ORDER and RETURN IF MATCH.
Therefor, it will run the modified classes.dex
AegisLab Antivirus Free and Premium can detect Master Keys Vulnerability!
Keep your engine and signature up to date please.
https://play.google.com/store/apps/details?id=com.aegislab.sd3prj.antivirus.free
https://play.google.com/store/apps/details?id=com.aegislab.sd3prj.premium
Analyzed by Ohoh and Rex



 Follow
Follow
I often visit your blog and have noticed that you don’t update it often. More frequent updates will give your site higher authority & rank in google.
I know that writing articles takes a lot of time, but you can always help yourself with miftolo’s tools which
will shorten the time of creating an article to a
couple of seconds.
What’s up to every body, it’s my first visit of this web site; this
website carries awesome and genuinely excellent information in favor of readers.
I have noticed you don’t monetize your page, don’t waste your
traffic, you can earn extra bucks every month because you’ve got high quality content.
If you want to know how to make extra money, search for:
Mertiso’s tips best adsense alternative
I do not know whether it’s just me or if perhaps everyone else
experiencing problems with your website. It seems
like some of the written text on your posts are running off the screen.
Can someone else please comment and let me know if this is
happening to them too? This could be a problem with my internet browser because I’ve had this happen previously.
Appreciate it
like this
Pingback: Daniel Beaulieu